To celebrate the 1-year anniversary of my post at Malware Blog, I am reposting this article here at AVSecurityProductManager.com:
How Big will the Android Malware Threat Be in 2012?
by Menard Osena (Solutions Product Manager)In August 2011, we released our Snapshot of Android Threats, which stated that there was a significant increase in the number of Trojanized Android apps and actual malware targeting the Android platform.
In our 12 Security Predictions For 2012, we mentioned that smartphone and tablet platforms, especially Android, will suffer from more cybercriminal attacks.
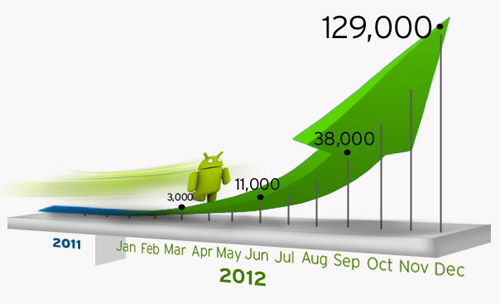
In our continuous monitoring of this threat, we soon noticed that the problem was growing at an alarming rate. From a mere handful of malicious apps at the start of the year, it skyrocketed to more than a thousand malicious Android apps by the middle of December 2011. The average month-on-month growth rate for the second half of 2011 was more than 60%.
If this growth rate is sustained this year, then 2012 will definitely be an “exciting” year forAndroid. Why is this so? If current trends hold, we may be able to see more than 120,000 malicious Android apps by December.
There are several factors that are causing this explosive growth:
- The increasing popularity of Android, as highlighted both by the number of total downloaded apps (more than 10 billion via the official Android Market) and the number of users and activations, as stated by Gartner and Google Senior Vice President of Mobile Andy Rubin.
- The openness of the Android app distribution model. Unlike other mobile OSes, users are free to install applications without passing through any filtering process. This lowers the barriers to installing malicious apps considerably.
- The cybercriminal mindset: Bad guys attack where the money is.
2011 already saw a wide variety of threats emerge for Android, as we discussed in our year in review. Android malware is definitely here to stay for 2012.
Original Post: TrendLabs Security Intelligence Blog: How Big will the Android Malware Threat Be in 2012?
Image Credit: blog.trendmicro.com
Additional personal insights to follow here at AVSecurityProductManager.com
Comments are closed.