I got this interesting email spam last week…
Subject: Your password on Pinterest Successfully changed!
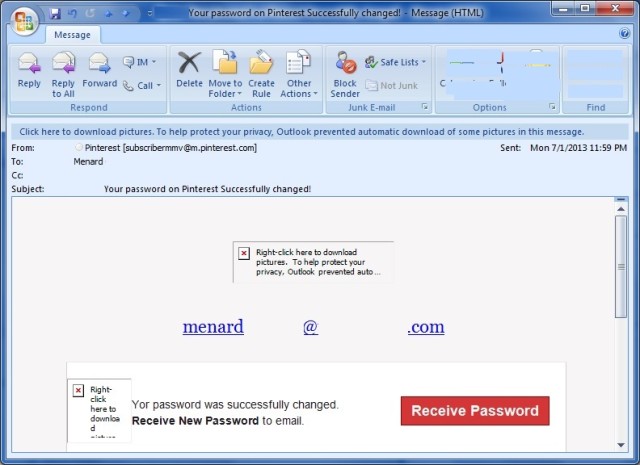
Image 1. Suspect email sample
I feel something is fishy (and phishy too) with the suspect email above. I don’t use this email address for social media accounts (Facebook, Twitter, Google+, Linkedin or Pinterest) so it is very unlikely to have Pinterest notification sent to this mailbox. I also find it weird that I need to click something to receive the password. I may be used to the normal website reset password mechanism (change password on the fly) so this suspect email really intrigued me. My AV and InfoSec training kicked in and I did some basic cyber-sleuthing 🙂
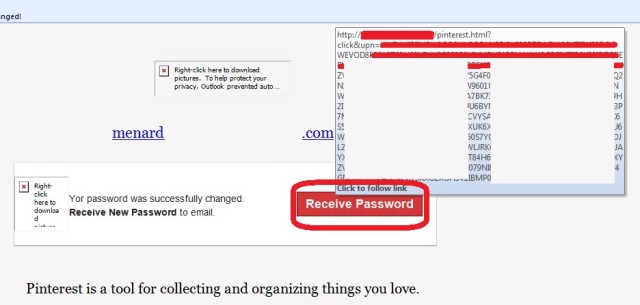
True enough, hovering around the Receive Password button as well checking all the links the inside the suspect email, I verified that all links DO NOT go to official Pinterest website but to another unrelated domain instead. URL/links are also strange and very long (contains all caps hexadecimal strings).
Image 2. Screen capture showing more details of suspect email (showing URL/link, link sanitized)
Some InfoSec and product management insights: Email spam is very much alive today. They have evolved a lot; from the traditional good old pharmacy and replica item related offers to a more sophisticated kind of attack. I am not sure if this one was a normal “low-hanging fruit” type of phishing or a more elaborately laid spear-phishing trap but I think (and hope) it was neither.
Good Practices Affirmation:
- Segregate email addresses and usage. Is it _NOT_ advisable not to mix email addresses/mailboxes for work and for social media accounts. I am a full-time InfoSec dude/Product Manager but that does not prohibit me from being active in social media. It’s good that I made it a habit to have another mailbox for my social media related accounts and separate it from work related mailbox
- Investigate before you click! Do not trust, always verify!!! Maybe its basic internet safety training or call it paranoia, but I really check most (if not all) of the links/URL I receive from untrusted sources before I click them. Sometimes I use URL-expanding applications (e.g LongURL) to get more details on shortened links. Whois, SiteSafety and other related websites (e.g WoT) are great tools to help individuals if they want check the suspected links and websites further.
Fast forward to July 3 2013…
A colleague posted a blog entry on TrendLabs Security Intelligence Blog. And so this Pinterest spam was indeed related to Blackhole Exploit Kit (Kridex, Blacole, Cridex).
Darn!!! This email might not be “the usual” spear-phishing after all (and I might really be a target). APT? APT!
Your Security Product Manager is really paranoid 🙂
Until next blog post…