Cryptocurrency-Mining Malware: 2018’s New Menace?
by: Menard Osena

Will cryptocurrency-mining malware be the new ransomware? The popularity and increasing real-world significance of cryptocurrencies are also drawing cybercriminal attention — so much so that it appears to keep pace with ransomware’s infamy in the threat landscape. In fact, cryptocurrency mining was the most detected network event in devices connected to home routers in 2017.
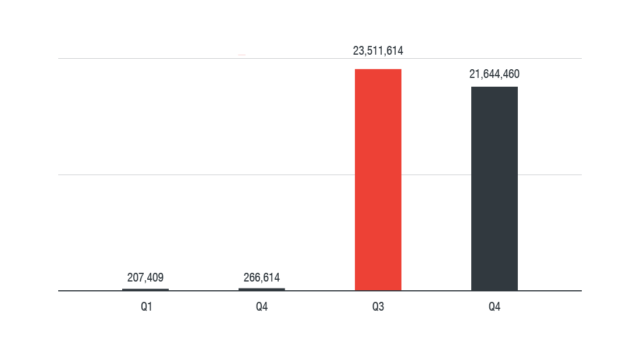
Figure 1. In 2017, cryptocurrency mining was the most detected network event in devices connected to home routers (based on Trend Micro Smart Home Network feedback)
What started out in mid-2011 as an afterthought to main payloads such as worms and backdoors has evolved into such an effective way to profit that even cyberespionage and ransomware operators, and organized hacking groups are joining the bandwagon.
Bitcoin, for instance, was valued at around US$1,000 in January 2017 but has since ballooned to over $11,000 today. It even peaked at a record $20,000 per bitcoin. Monero’s (XMR) story was the same, with a value that shot up from $13 in January 2017 to $325 in February 2018. The volatile yet sharp increases in their value give the shift some weight. Where there’s money to be made, expect threat actors to try to be in on it.
Their use of cryptocurrency-mining malware and its meteoric ascent in the threat landscape is a case in point. As shown below, cryptocurrency-mining malware’s prevalence gained momentum, peaking at 116,361 in October 2017 before stabilizing throughout November and December. We detected the most cryptocurrency-mining malware in Japan, India, Taiwan, the U.S., and Australia.
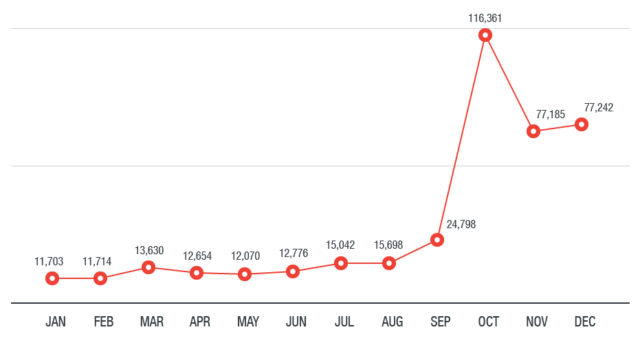
Figure 2. Cryptocurrency-mining malware detections in 2017
(based on Trend Micro Smart Protection Network)
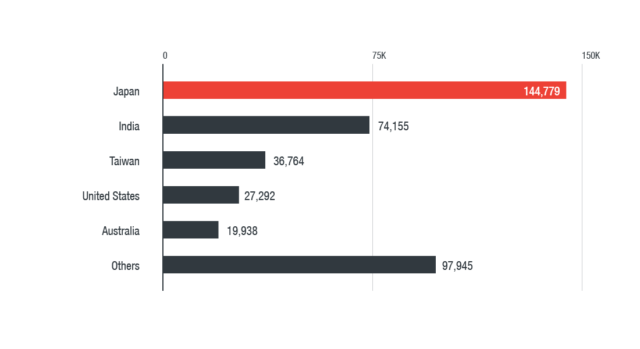
Figure 3. Country distribution of cryptocurrency-mining malware detections in 2017
(based on Trend Micro Smart Protection Network)
Other paradigm shifts are expected to be signs of things to come for cybercriminal cryptocurrency mining: the abuse of legitimate and grayware tools, particularly Coinhive, the penchant for mining Monero, and the emergence of fileless cryptocurrency miners.
From Bitcoin to Monero
Coinhive provides users and companies an alternate monetization platform by offering an embeddable JavaScript code that will use the site visitor’s CPU to mine Monero. This method’s apparent convenience and customizability did not escape cybercriminals. In fact, malicious versions of Coinhive’s miner were reported to be the sixth most common malware in the world, hitting even the official websites of organizations in the U.S. and U.K. as well as cloud servers of high-profile companies. The miner also spread through malvertisements.
It’s no surprise that Monero would be Coinhive and the cybercriminals’ cryptocurrency of choice. The algorithm used to mine Monero — CryptoNight — is designed to be resistant to ASIC mining. It’s thus more suited to calculating hashes on consumer hardware CPUs.
While bitcoin mining is still technically possible by using CPU and graphics processing unit (GPU) or a combination of both, it’s no longer as viable as it was especially when held up against dedicated rigs using application-specific integrated circuit chips (ASICs) and cloud-mining providers. Meanwhile, a miner can run 24/7 for a year, and it still won’t yield a single bitcoin.
Monero is also more pseudonymous than bitcoin. Its use of ring signatures makes it difficult to follow trails in transactions made through Monero’s blockchain — address, amount, origin, and destination, senders and recipients, to name a few.
Fileless Cryptocurrency-Mining Malware
Just like how ransomware matured, we’re starting to see the use of notorious exploits and methods for deploying fileless malware to install miners. Coinhive notes, for instance, that 10-20 active miners on a website can turn a monthly profit of 0.3 XMR — or $97 (as of February 22, 2018). An army of zombified systems translates to more illicit payouts.
A cryptocurrency-mining malware we found last year, which exploited EternalBlue for propagation and abused Windows Management Instrumentation (WMI) for persistence, is an example of this. In fact, the Monero-mining Adylkuzz malware was reportedly one of the first to exploit EternalBlue before WannaCry. The longer the system and network remain unpatched, the more they are at risk of re-infection.
A typical infection chain in fileless cryptocurrency-mining malware, as shown below, involves loading the malicious code to the system’s memory. The only physical footprint indicating an infection is the presence of a malicious batch file, an installed WMI service, and a PowerShell executable. For propagation, some use EternalBlue exploits, but we also saw others employing Mimikatz to collect user credentials in order to access them and turn the machines into Monero-mining nodes.
Indeed, vulnerabilities will also be one of the main doorways for cryptocurrency-mining malware. This is demonstrated by the recent intrusion attempts we observed on Apache CouchDB database management systems. JenkinsMiner, a remote access Trojan also toting a Monero miner and targets Jenkins servers, reportedly earned its operators over $3 million worth of Monero.

Figure 4. A typical infection flow of fileless cryptocurrency-mining malware
(click to enlarge)
Thwarting Cryptocurrency-Mining Malware
Cryptocurrencies aren’t inherently prohibited, at least in many countries. Given their decentralized nature, they have regulatory frameworks from which their trade is legally overseen. Mining them illicitly through malware, however, is a different matter.
But while cryptocurrency-mining malware’s impact may not be as palpable or damaging as ransomware’s, they are no less of a threat. In December last year, the Loapi Monero-mining Android malware showed how they could physically damage a mobile device.
But cybercriminal cryptocurrency mining isn’t just about device wear and tear, or even the power consumption involved. It’s also a reflection of the ever-evolving technology landscape and the risks and threats that can come with it. And just like ransomware, we expect cryptocurrency-mining malware to be as diverse as they are common, using a plethora of ways to infect systems and even inadvertently turn their victims a part of the problem. This highlights the need to complement security mechanisms with defense in depth, adopting best practices not only for enterprises and everyday users but also the devices’ design and equipment manufacturers.

Figure 5. Trend Micro’s proactive solutions against fileless cryptocurrency-mining malware
(click to enlarge)
Trend Micro XGen security provides a cross-generational blend of threat defense techniques to protect systems from cryptocurrency-mining malware. It features high-fidelity machine learning to secure the gateway and endpoint, and protects physical, virtual, and cloud workloads. With capabilities like web/URL filtering, behavioral analysis, and custom sandboxing, XGen protects against today’s threats that bypass traditional controls, exploit known, unknown, or undisclosed vulnerabilities, either steal or encrypt personally-identifiable data, or conduct malicious cryptocurrency mining. Smart, optimized, and connected, XGen powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Original Post from: Trendlabs Security Intelligence Blog
Full post link Cryptocurrency-Mining Malware: 2018’s New Menace?
Additional #tech #infosec #security insights on #Cryptocurrency #Bitcoin #Mining to follow soon, so watch out for it 🙂








 Smart Home Network
Smart Home Network